Ansible Facts and vaults are important features used in Ansible . Both have different use cases and importance in this article we will be covering Ansible facts and vaults and their use cases in real-life scenarios.

Ansible facts
Ansible facts are data gathered about target nodes (host nodes to be configured) and returned back to controller nodes. Ansible facts are stored in JSON format and are used to make important decisions about tasks based on their statistics. Facts are in an ansible_facts variable, which is managed by Ansible Engine. Ansible facts play a major role in syncing with hosts in accordance with real-time data.
Let’s say an example case in which you are trying to install an nginx webserver using Ansible but you have n number of target nodes which consist of Debian and Redhat-based distribution.
So if you are trying to install nginx in the Debian server you need to use the apt module but in the case of redhat you need to use the yum module.
Like the above example there will be certain situations where the task completely depends on the remote worker node configurations and data in such cases we use the Ansible facts.
Ansible facts using Ad-hoc commands
Access Ansible facts using ad-hoc commands
The setup module fetches all the details from the remote hosts to our controller nodes and dumps them directly to our screen for the facts to be visible to users.
ansible all -m setup
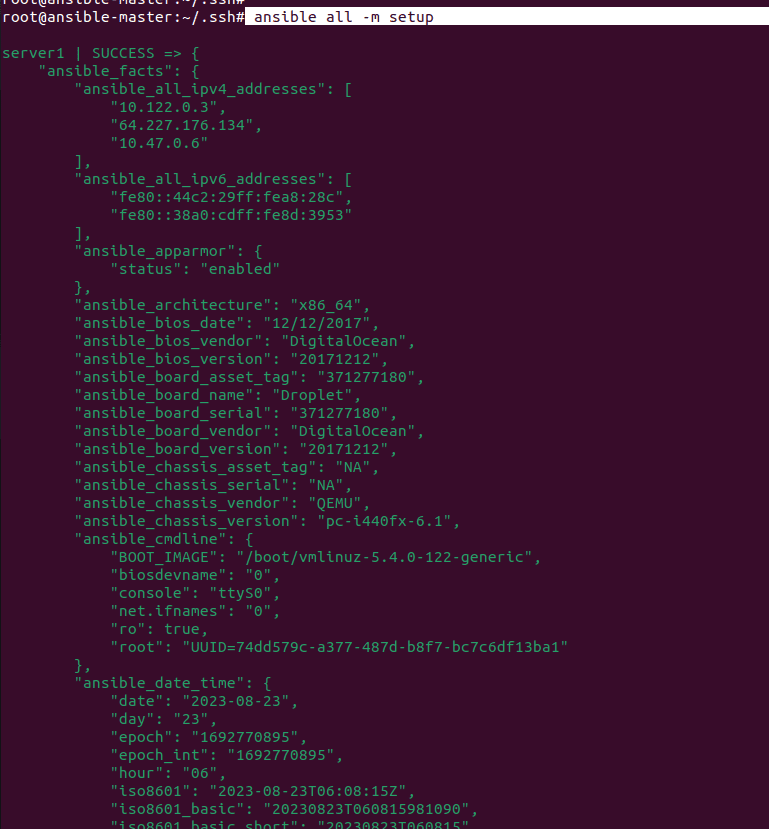
I am using some of the filter arguments to filter out the output of the setup command to get my worker node information like the node name of the worker node the distribution etc. as shown in the below screenshots.
ansible all -m setup -a ‘filter=ansible_nodename’
ansible all -m setup -a ‘filter=ansible_distribution’
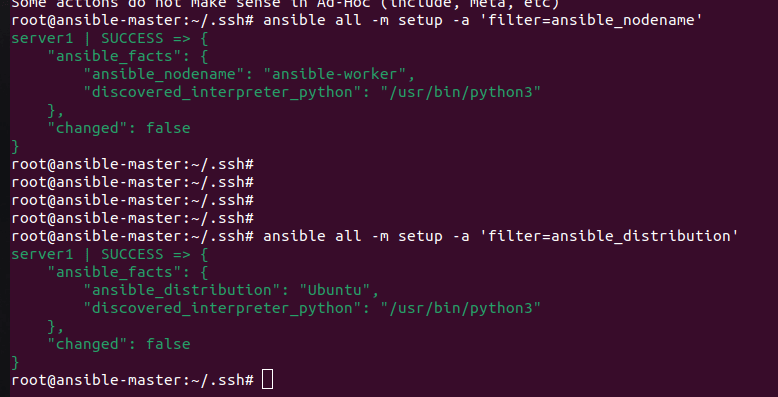
As you can see in the above image the details about my worker node are provided as a JSON output to the screen.
Ansible facts in a playbook
Here is the example playbook that uses the ansbile_facts module to get the os_family details and install the nginx package based on the distribution (Redhat or Debian) using the
- hosts: all
tasks:
- name: Install Nginx on RedHat
package:
name: "nginx"
state: present
when: ansible_facts["os_family"] == "RedHat"
- name: Install Nginx on Debian/Ubuntu
package:
name: "nginx"
state: present
when: ansible_facts["os_family"] == "Debian"
Here, the script will collect information about the system using Ansible facts and then perform the operation accordingly. When installed on RHEL systems, it automatically skips the Ubuntu-based package and vice versa. Similarly, you can use the Ansible facts to perform an operation if the system has a minimal amount of resources available.
There are also many use cases for Ansible facts if you want the os information of all the nodes configured under your master node you can use this playbook.
- hosts: all
tasks:
- debug:
var: ansible_facts["distribution"]To access the variables from Ansible facts in the Ansible playbook, we need to use the actual name without using the ansible keyword.
ansible_facts[“ansible_distribution”] ❌
ansible_facts[“distribution”] ✔️
Ansible vaults
Ansible Vault is an Ansible feature that helps you encrypt confidential information without compromising security.
We have created many playbooks in our recent articles but we were storing confidential information like the database name, passwords etc. in plain text which makes it insecure.
Encrypting a playbook.
The ansible-vault create command is used to create the encrypted file.
ansible-vault create playbook.yaml
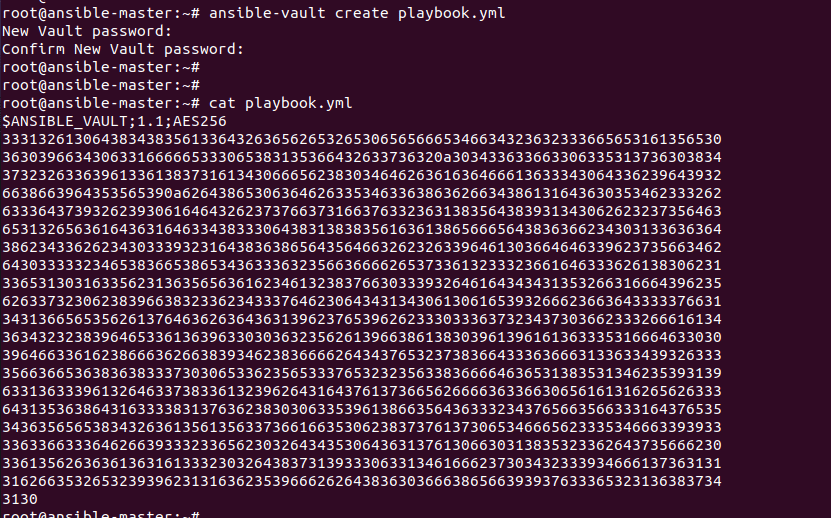
As you can see in the above image when I tried to fetch the contents of the file it showed encrypted values.
You can also use ansible-vault encrypt playbook.yml if the playbook is already created
Decrypting a file
The ansible-vault decrypt the command is used to decrypt the encrypted file.
Followed by the password used to encrypt.
ansible-vault decrypt playbook.yml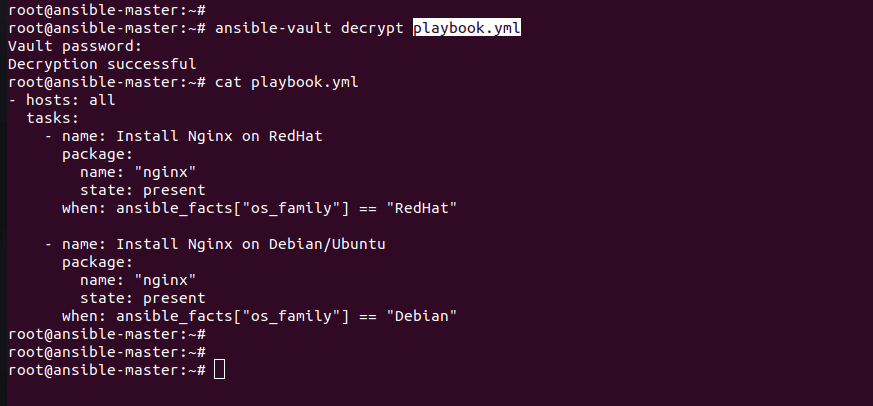
Editing the encrypted file
If the file is encrypted and changes are required, use the edit command.
ansible-vault edit playbook.ymlReset the file password
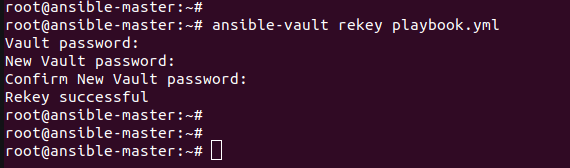
If we enabled the password and want to reset it use the command to reset the encrypted file password.
ansible-vault rekey playbook.yaml
If you run an encrypted playbook it will ask for the password so rather than entering the password every time of execution of the playbook Passwords can be specified with a file or a script (the script version will require Ansible 1.7 or later). When using this flag, ensure permissions on the file are such that no one else can access your key and do not add your key to source control.
ansible-playbook site.yml –vault-password-file ~/.vault_pass.txt
Summary:
That’s it, in this article, we have discussed the use cases of both ansible facts and vaults in real-life scenarios.



